Why we need private email attestation
An insight into our motivation for building privacy tools. This post focuses on the issues with email and the missing technological links. Our private email attestation tool bridges a lot of these gaps.

Electronic mail has been around for many decades now. Today, the first important step in onboarding a new employee in any organization is setting up their work email. Over the years, email received from an address with the official domain of a company has become a way to check legitimacy. However, there is a myriad of issues with email privacy still. In many organizations, an IT administrator can scan and read the emails sent and received by most employees. Regardless, an official company email is still one of the best ways to establish a relationship between the owner of the email address and the company whose domain the email ends. Other ways to establish such a connection include an official ID, word of mouth, social assurances, etc. However, these are more intrusive and sometimes require other people.
Social connections and confidence in the real world is based on trust. Your friend introduces you to someone who works at, let's say, SnApple. You trust this piece of information as it comes from a trusted source, your friend. Your friend could tell you that they could get answers about the inner workings of SnApple or how they treat their employees from an acquaintance who works at SnApple. Perhaps you're considering a new job at SnApple and your friend's acquaintance will provide you the information through your friend, but they don't want you to know their identity. This is a scenario that is easy to resolve in the real world. You don't need to see the person who works at SnApple and provides the inside scoop on the company. And they don't need to know who you are. All of this works because you both have a common trusted link, your friend, who certifies relevant information (the acquaintance's employer) and provides a common communication link.
Consider the scenario above, but in a digital setting, it seems like a paradox to keep someone's identity private but still know that they work at SnApple. Reddit and Team Blind are both pseudonymous social networks. Team Blind, in particular, is a professional social network where conversations primarily focus on inside scoops on company culture, employee compensation, and any other gossip about people's employers. Due to the missing link of trust here, there is no way to legitimize your information source. In high stake scenarios, establishing trust is critical. If you're deciding to move across the country for a new job, you better ensure it's worth it. And consequently, the source of the information matters. Or what if you're a journalist talking to a whistleblower on the dark web, and you're not sure about the legitimacy of the whistleblower's claims (for ex. overworking in SnApple factories) and their association with the reported issue (if they work at SnApple). There is no way all whistleblowers will violate their NDA or risk getting fired or sued by a huge corporation, and neither should they. So sending a picture of their ID etc. can be quickly dismissed as an option. What if they send you an email from their work email? Aha! They open their email and send you a benign-looking verification email. Not so fast; the IT administration overlords can quickly sniff through this information whenever they want and catch the whistleblower.
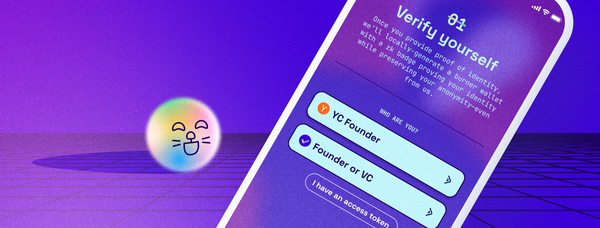
What if there was a magical internet attestation oracle? You could go up to this oracle and ask, "Hey! Should I trust this advice of u/throwawayTomorrow556 on a potentially life-changing move across the country for a new job?" The oracle tells you to trust the information or not. Through the magic of cryptography, we can cook up something not too far away from this. We are iterating through the first publicly available, free for all, private email attestation tool. This is the missing link required to fix a lot of email privacy issues. For example, many phishing attempts [1, 2, 3] try to convince people to sign in using their email and associated password to a portal, clearly to steal this information for nefarious purposes. Users fall for such a scam not due to a lack of awareness or expertise but because of this broken system. Many communities (ex. Discord college communities, gated facebook groups, any student/employee discount programs, etc.) authenticate a new user's association with an employee, university, etc. using the emails ending in the official domain. This is a broken system because of two main reasons. First, it makes the masses believe that their email and password are information they could be asked for authentication at any endpoint for services to establish the link between them and the organization the gated community is meant for. Secondly, they don't need you to log in to your email address. All they need is proof that you own an email that ends with "@SnApple.com".
To summarize, now you have a magic oracle that lets you generate proofs guaranteeing that you own an email address associated with an organization. You can very quickly authenticate people's association with their employers/universities. This makes the path to building a lot of privacy-preserving applications easy. Some examples are anonymous chat rooms for people in the same organization, anonymous voting systems, private authentication for any high-stake application such as whistleblowing, etc. The guarantee of privacy is mathematical and unlikely to be violated. In a coming blogpost, we will talk about how this magic oracle works and the guarantees it provides!