Tea, tech, and secrets: how ketl onboards founders and VCs with zk
Meet ketl: private work-based socials powered by zk proofs. We have built the first anonymous credentials for all YC founders. Find out more and download on TestFlight!
We just shipped the first anonymous credentials for YC founders. Let's dive into the "why?" and "how?". Work-based social networking has made a huge resurgence in the last few years, possibly owing to the rise in remote work. Work-based social platforms, like LinkedIn, Fishbowl, and Blind, have become pivotal to professional networking and information sharing. They create spaces for employees to connect, engage, and share industry insights, fostering a sense of camaraderie beyond geographical boundaries.
However, mainstream platforms come with glaring issues that mar the digital utopia they promise. Privacy and censorship are among the biggest concerns. Most of these platforms were not constructed with a privacy-first approach. They store colossal amounts of user data, leaving privacy hanging by a thin thread, susceptible to the slightest misstep. They also lack resistance against censorship, thereby posing a threat to free speech and honest discourse. Two stark examples of these issues manifest in the case of Blind and Glassdoor.
Blind, a workplace social network that facilitates anonymous discussions on sensitive topics like salaries and employee misconduct, has had a significant data breach. They left a database server unsecured, exposing user account information, including corporate email addresses. This security lapse affected users' privacy from over 70,000 companies, including top tech companies. Blind, which was supposed to be a safe haven for candid conversations, turned into a risk for its users.
Similarly, Glassdoor, an anonymous review site, faced a legal order to hand over the identities behind six scathing reviews of a toy company, Zuru. Such instances threaten Glassdoor's privacy policy and its very existence. Despite Glassdoor's efforts to resist such subpoenas, this case highlights the precariousness of user privacy on the platform.
ketl: A Platform Brewed in Privacy and Censorship Resistance
We propose a different approach to work-based social media in light of these issues. We believe in the principles of "do no harm" and, crucially, "can't do no harm." At the core of ketl are privacy and censorship resistance. We understand the value of anonymous discourse and respect your digital privacy. ketl doesn't just provide a platform for open conversation; it safeguards your right to privacy and freedom of speech.
Harnessing the power of anonymous credentials built using zero-knowledge proofs, ketl maintains user privacy. We ensure anonymity by verifying claims without revealing identifiable information on the user's identity, making ketl a fortress for your private conversations. Additionally, we use blockchain and the InterPlanetary File System (IPFS) as our backbone for censorship resistance, upholding your right to voice your thoughts and experiences.
ketl isn't just another work-based social media platform. It's a fight against the status quo of compromised privacy and stifled voices. Better technology exists now, so there is no need to rely on old broken platforms and put your privacy at risk. This is an invitation to a more secure, honest, and engaging work-based social media experience. It's time to brew, and everyone's invited to spill the tea!
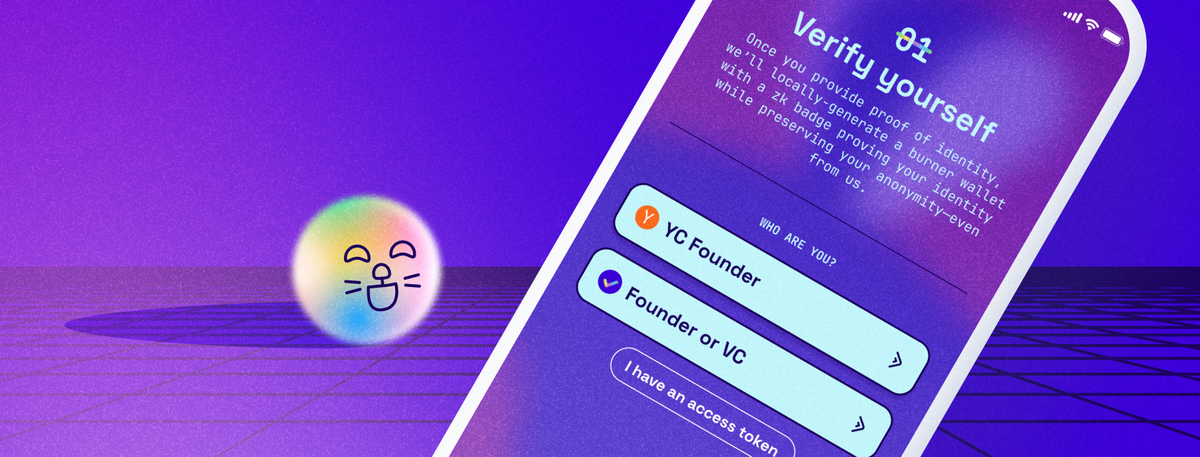
Onboarding and Identity Verification: Unlocking the Gates of ketl
The first step in the ketl experience is getting users onboarded onto the app. We understand the importance of ensuring that users have relevant badges that reflect their identity, such as "Verified YC Founder" or "Verified Founder" (with more badges to come in the future). To this end, we allow individuals to verify their identity first, and only if the verification succeeds can they create a ketl account. Our system and protocols are designed so that even we do not know which person has what handle on ketl. This ensures that in the future, neither can this information be leaked nor can we be sued for it, truly upholding user privacy.
Now, let's briefly discuss the general architecture of ketl. Every user action is recorded on the blockchain, where each post becomes a transaction. The associated data of each post has a content identifier (CID) on the InterPlanetary File System (IPFS). This architectural design choice allows users to run their own nodes or choose their own RPC to perform all posting-related actions. As we roll out ketl to a wider audience, we will add more in-app options to facilitate this. This decentralized approach empowers users and ensures that ketl remains censorship-resistant.
Once users are on the platform, they gain access to a vibrant community of individuals in the startup ecosystem. They can openly discuss many crucial questions here: Which investors to raise funds from? Which incubators to apply for? Where to find co-founders? What are fair terms for seed rounds in the current macroeconomic conditions? ketl fills a void in existing platforms by providing a private, high-value community conducive to honest discussions. This opens the door for many possibilities for the platform: ranging from a review system for investors to a space that helps individuals avoid toxic workplaces.
However, an essential question in anonymous communities is how to prevent toxicity and unpleasant behavior. For ketl, we prioritize creating a respectful environment where users can share information honestly without fear. To achieve this, we are exploring an incentives structure that promotes content resonating with the community while maintaining a sense of comfort and inclusivity for all users.
Now, let's dive into the onboarding flow, focusing on Y Combinator (YC) founders and founders at large for this current season of ketl. We will introduce similar onboarding flows for investors/VCs in the near future. For YC founders, we offer three primary onboarding methods:
- Using your "[email protected]" email: This method requires founders to control this particular email address with their company's domain. This requirement aligns with YC's directory, ensuring a streamlined onboarding experience.
- Leveraging the Orange DAO alumni gem: The Orange DAO is an NFT possessed by YC founders who are part of the collective. This venture structure aims to scout and support young crypto startups. By utilizing this NFT, ketl enables a seamless onboarding process for Orange DAO members.
- Utilizing your Twitter account listed in the official YC directory: This method allows YC founders to onboard using their Twitter accounts, provided that they are part of the YC directory.
By embracing these onboarding flows, ketl aims to create an inclusive and diverse community, fostering meaningful connections among individuals with shared experiences and aspirations. We will be launching other fine-grained credentials as well, such as "Top YC Founder", "Top Investor" and credentials indicating company and fund stages.
Let's look at the onboarding flows in some more detail.
Email Verification
For YC founders, we leverage the public founder directory published by Y Combinator. This database helps us create an "anonymity set" of founders who possess the YC credential. We curate an allowlist of their email addresses for other founders and VCs.
To sign up using the email method, you enter your "[email protected]" email address. We send an attestation token to this email that you can enter into the app. But how do we ensure privacy? When you enter your token, we don't directly receive it. Instead, we receive a privacy-preserving proof called zero-knowledge/zk proof, which confirms that you have a valid token from an approved set without revealing the specific token you possess. This process guarantees privacy, as we cannot link your email address to your ketl account.
This proof is then combined with a password, creating a nullifier: this allows us to limit the creation of multiple accounts. Once the zk proof is verified, we generate a burner wallet for you and mint a ketl founder/VC token. This burner wallet becomes your means of interacting with the blockchain via the app, and your user handle is associated with it. This ensures a safe and anonymous experience on the app.
Orange DAO Alumni Gem
The list of Orange DAO members is public, and they all possess an alumni gem NFT. Like SealCred, once you link the wallet containing this NFT, your device generates a zk Proof of ownership for the NFT. This proof is then submitted to us. If you're part of Orange DAO, you can securely and anonymously verify the wallet associated with your Orange DAO gem. This method ensures that no one, including us, ever knows which on-chain Orange DAO member address is associated with what ketl account, preserving your privacy on all future ketl interactions. Unless you doxx yourself!
Once the zk proof is verified, we create a burner wallet for you and mint a YC founder token. This burner wallet becomes your means of interacting with the blockchain via the app, and your user handle is associated with it. This ensures a safe and anonymous experience on the app.
Twitter Account Verification
The final method for obtaining a ketl account is using your Twitter account, which is listed in the YC directory. When choosing this method, the app requests an OAuth token from Twitter to verify that you are indeed the owner of a Twitter account linked to a YC founder. Once this verification is completed, you receive a ketl sign-up token. Your device then generates a zk proof of ownership of a valid ketl token, allowing you to register for a ketl account and select a handle.
Once the zk proof is verified, we create a burner wallet for you and mint a YC founder token. This burner wallet becomes your means of interacting with the blockchain via the app, and your user handle is associated with it. This ensures a safe and anonymous experience on the app.
However, there is a potential risk of the anonymous token associated with it being tied to the time you created it, which can compromise your anonymity. We have implemented two practices to mitigate this risk and ensure privacy. Firstly, all early users must wait until an anonymity threshold is reached before their accounts are fully activated. This protects the privacy of those who were among the first to sign up.
Secondly, for all users, we strongly encourage waiting before taking your first 'action' on the platform, such as posting or upvoting. While you create your profile upon signing up, its activation occurs only when you perform your initial action. By waiting, you eliminate any assumption that could be made if you were to immediately post something sensitive. This deliberate delay in taking action helps ensure that your timing of sign-up and subsequent activities remain unrelated, safeguarding your anonymity and protecting your privacy on ketl.
We are committed to promoting candid discussions, fostering professional connections, and upholding the principles of privacy and freedom of speech in the digital world. To create a safer space for discourse, we put your privacy first, ensuring that your anonymous identity on ketl remains uncompromised. At its heart, ketl is about brewing ideas and conversations that matter, so join us today and let's spill the tea! Stay tuned to our upcoming blog posts, where we will dive deep into the technical details of our platform. ketl is available on testflight! If you're a YC founder, then you can sign up yourself! Other founders and VCs can request to join here.